Investigating a DNS DDoS Attack
Update: AT&T sent me a new modem which gave me a new IP address. All is fine now :)
ORIGINAL POST:
Last night I began noticing extreme slowness in traffic bound to Google Play Store. Strangely enough, all other network traffic was fine. Upon further investigation, I realized that my Sophos Home UTM was dropping hundreds of DNS queries on external (public) interface. Well, 32,968 DNS queries per hour or 549 queries per second. I only allow port 53 to internal clients and two static OpenDNS IP addresses. Intrusion prevention system is also doing its job and blocked malformed DNS packets. The UTM's CPU never spiked above 2% and RAM stayed in 10% - 20% range. So I knew I was in good shape. However, I had to investigate. This was my chance !!!
For cool factor, here's map generated using Splunk, showing where I received the queries from:
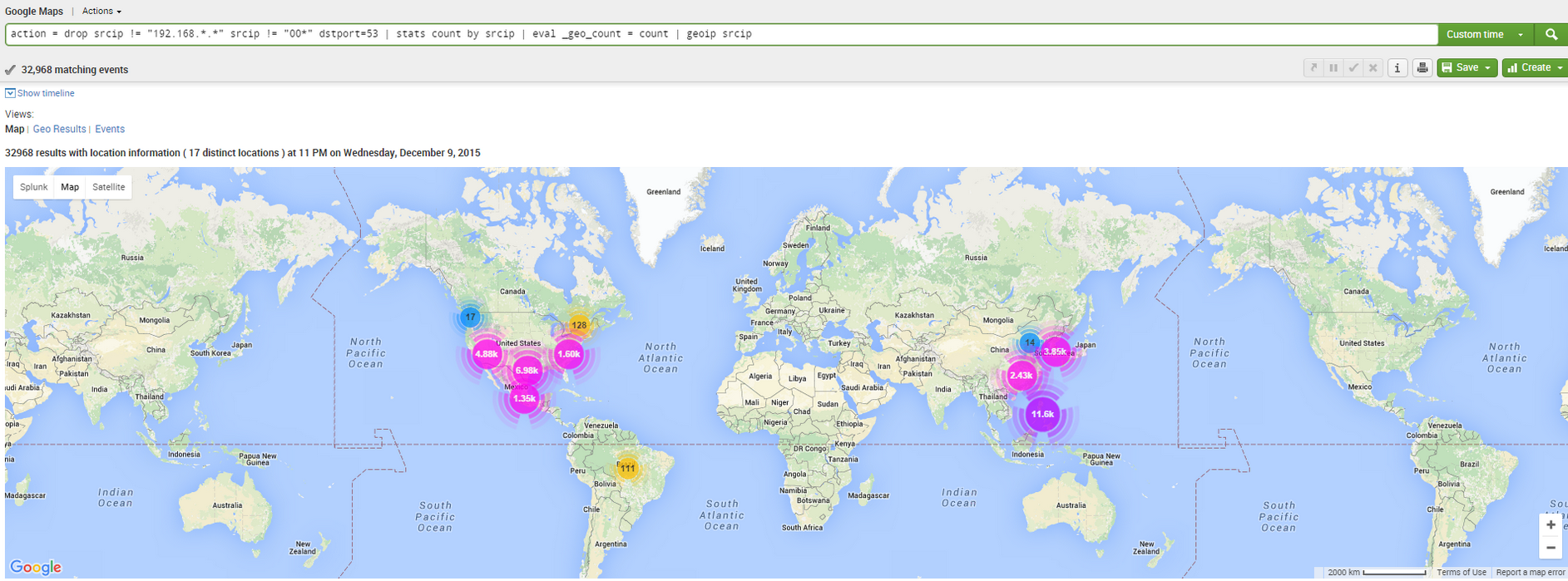
So, I SSH into my UTM and fired up TCPDUMP utility. TCPDUMP is like a command-line version of Wireshark. It can sniff packets, process them, and store them in your desired format. Since all packets I was interested in were DNS packets, here is the command I ran to capture all DNS traffic on my external (ETH01) interface:
tcpdump -i eth0 port 53
And result?
22:14:35.440155 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.440360 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.440554 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.440731 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.440910 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.441091 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.441292 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
22:14:35.441486 IP 183.60.233.137.7950 > sophosutm.domain: 9075+ [1au] ANY? hehehey.ru. (44)
As you can see, I'm am receiving queries from 183.60.233.137 requesting name resolution for hehehey.ru. https://who.is/ shows 183.60.233.137 is one of China Telecom IP addresses. In regards to our queried domain name, here is what VirusTotal.com has to say:
Latest URLs hosted in this domain detected by at least one URL scanner or malicious URL dataset.
For sure, 183.60.233.137 isn't the only IP address sending these queries. A quick search in Splunk
action="drop" dstport=53 |stats count by srcip
Results are astounding. Within last 24 hours, I received DNS queries from 163 different IP addresses. Top ten are as follows:
192.99.194.134 -- 23218 queries
63.217.89.18 -- 22192 queries
23.234.34.23 -- 20825 queries
103.6.249.142 -- 13506 queries
200.185.6.163 -- 11641 queries
200.185.6.131 -- 11463 queries
172.246.200.135 -- 9031 queries
113.20.145.39 -- 8696 queries
158.69.128.124 -- 6227 queries
219.135.58.151 -- 5815 queries
As much as I would like to investigate further, it's way too many IP addresses, most of which are from shared hosting providers. The IP addresses may have been spoofed to add more complexity to the matter. If Root Server Operations team couldn't go further than this step, I think I will stop here too. The DDoS attack is still continuing and AT&T hasn't given me a new IP address even after tens of modem reboots and phone calls. Alright, back to work !!!
